
2024-04-19 11:08:00 UTC
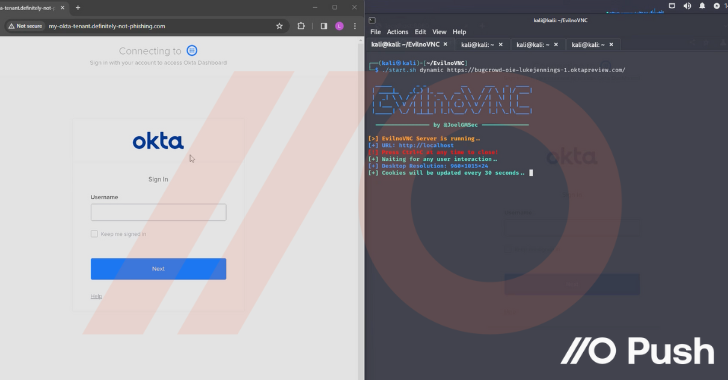
Attackers are now able to take control of businesses without needing direct access to the endpoint thanks to "networkless" attack techniques that focus on cloud apps and identities. This new approach allows attackers to compromise organizations without touching traditional networked systems. Before diving into the specifics of these techniques, it is important to understand why this shift is occurring.